dashboardwireguard-tunnelwireguard-dashboardwireguardwg-managervpnsite-to-siteobfuscationwireguard-vpn-setupwireguard-vpn
You can not select more than 25 topics
Topics must start with a letter or number, can include dashes ('-') and can be up to 35 characters long.
|
|
6 years ago | |
|---|---|---|
| docker | 6 years ago | |
| docs | 6 years ago | |
| wg_dashboard_backend | 6 years ago | |
| wg_dashboard_frontend | 6 years ago | |
| .dockerignore | 6 years ago | |
| .gitignore | 6 years ago | |
| CODE_OF_CONDUCT.md | 6 years ago | |
| Dockerfile | 6 years ago | |
| LICENSE | 6 years ago | |
| README.md | 6 years ago | |
| docker-compose.yaml | 6 years ago | |
| package-lock.json | 6 years ago | |
README.md
wg-manager
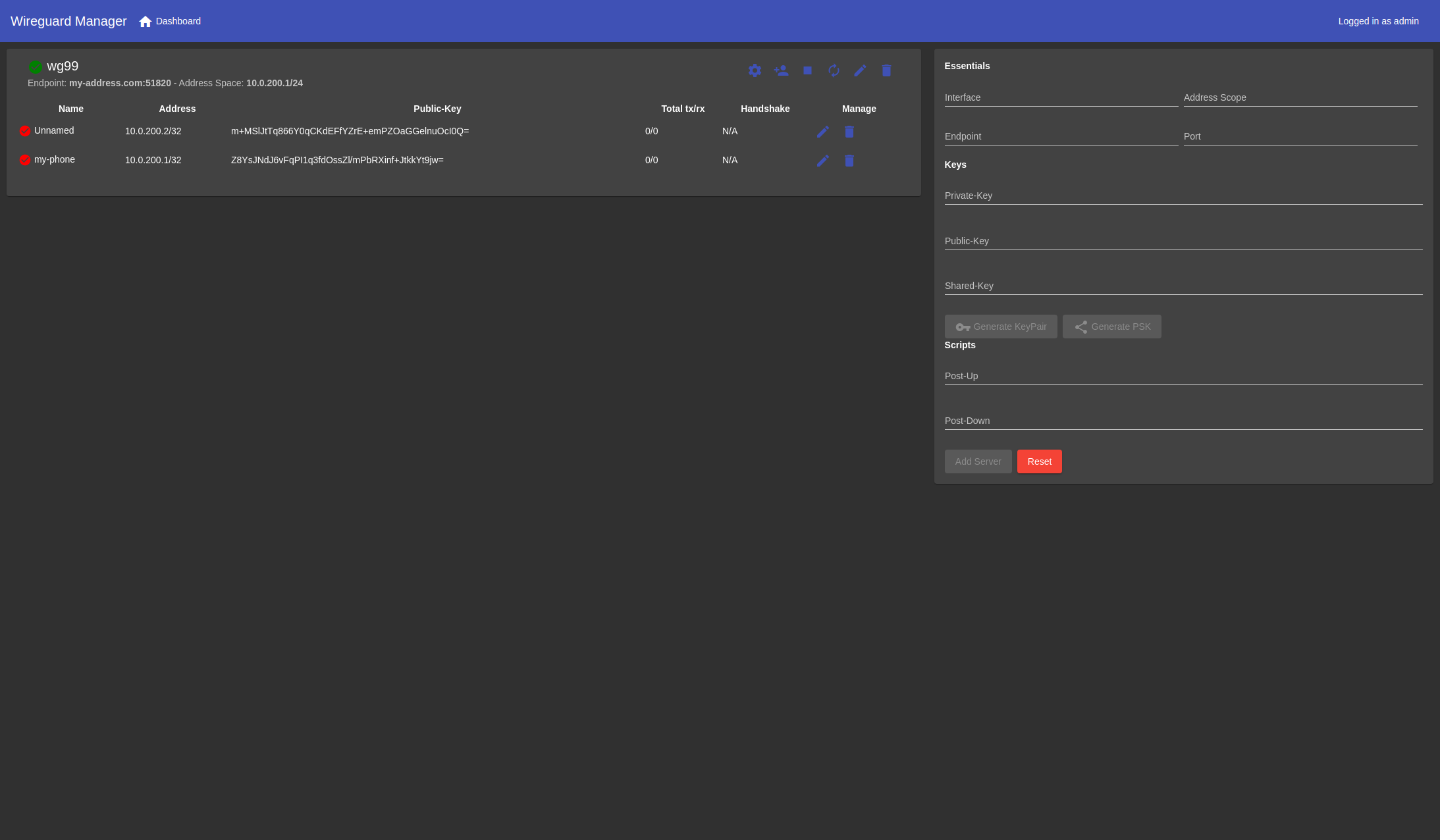
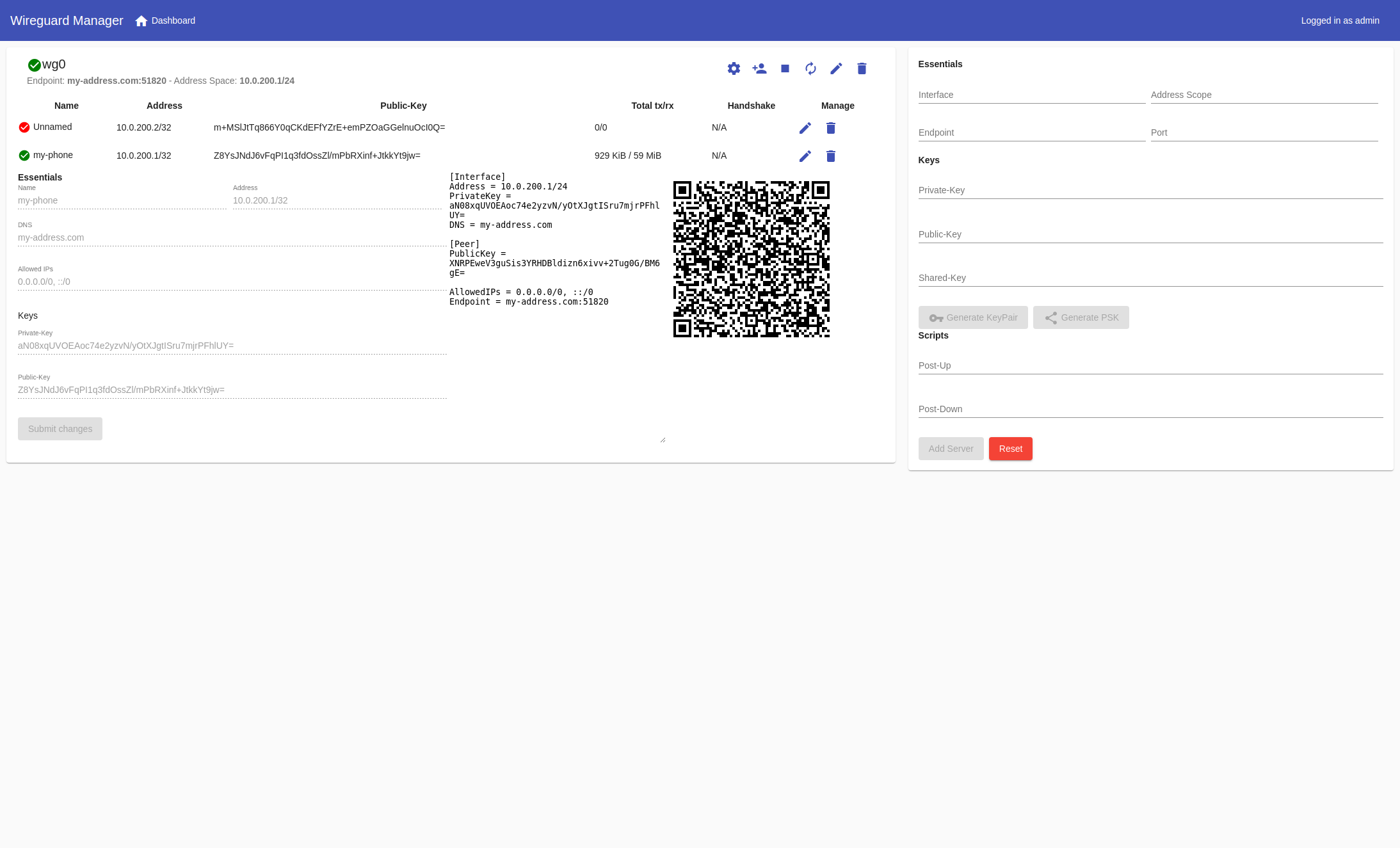
The wg-manager provides an easy-to-use graphical web interface to import, setup, and manage WireGuard server(s). See Here
The features of wg-manager includes:
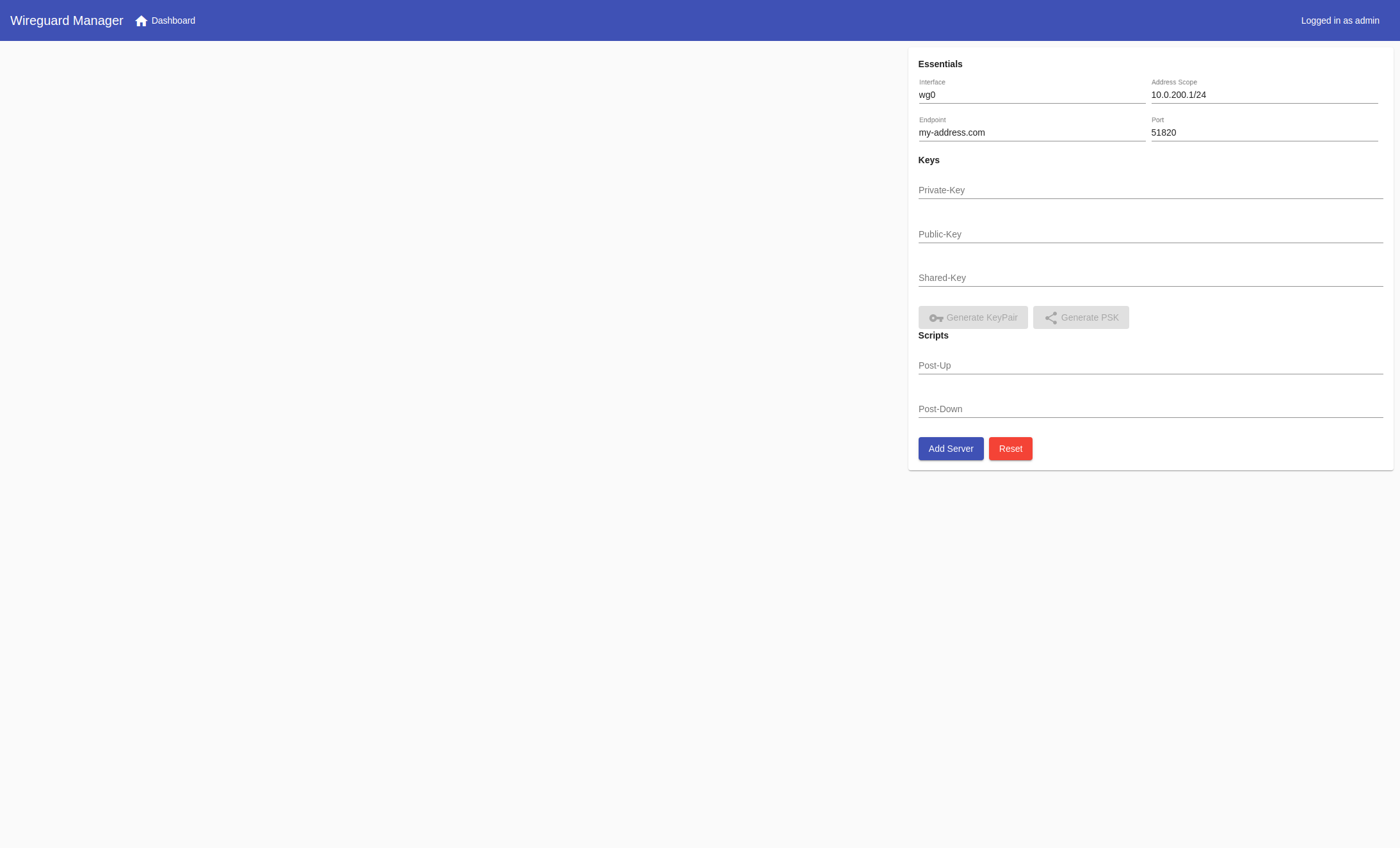
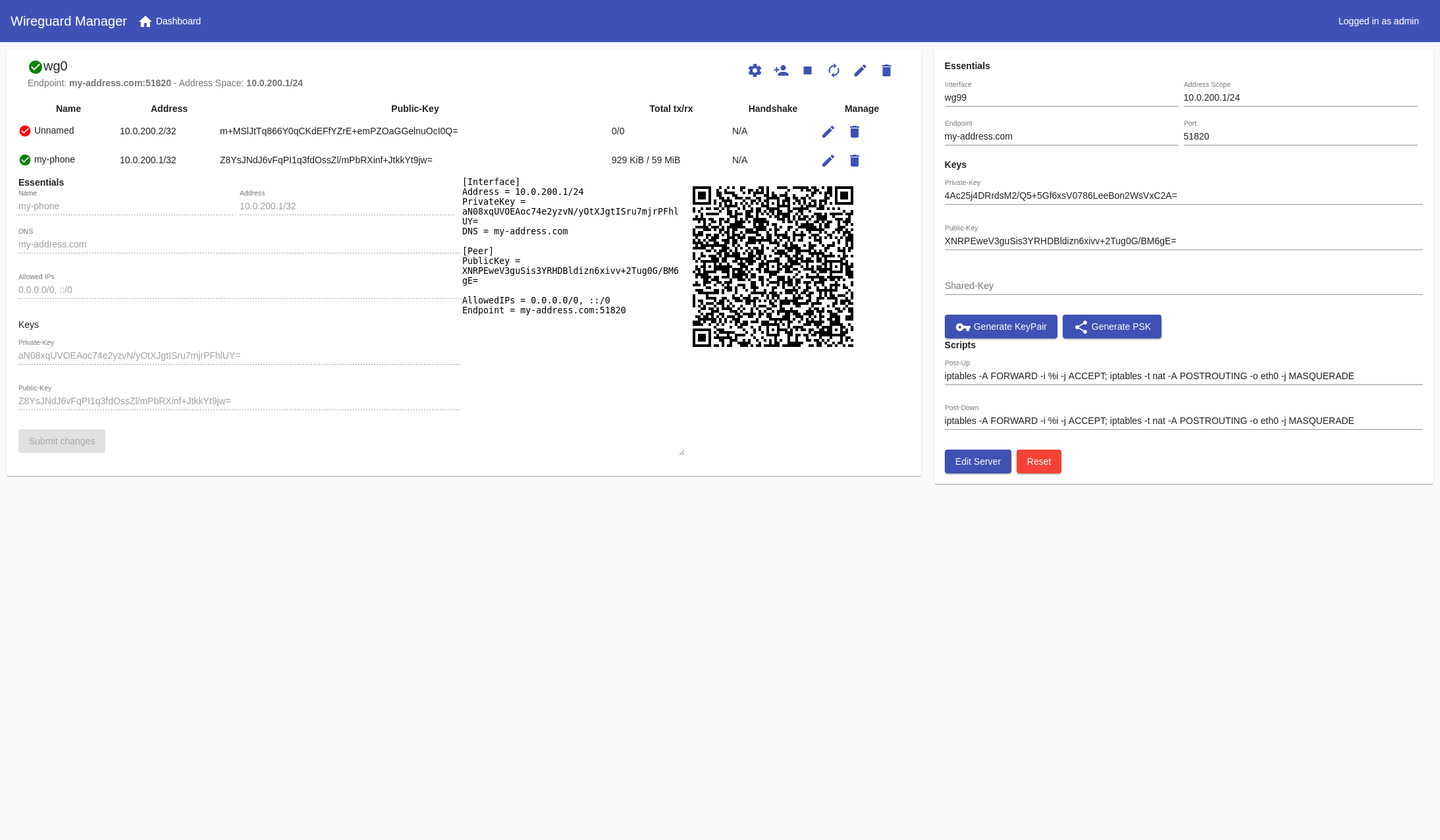
Server
- IPv4 and IPv6 support
- Create/Delete/Modify
- Start/Stop/Restart server
- Import existing configurations
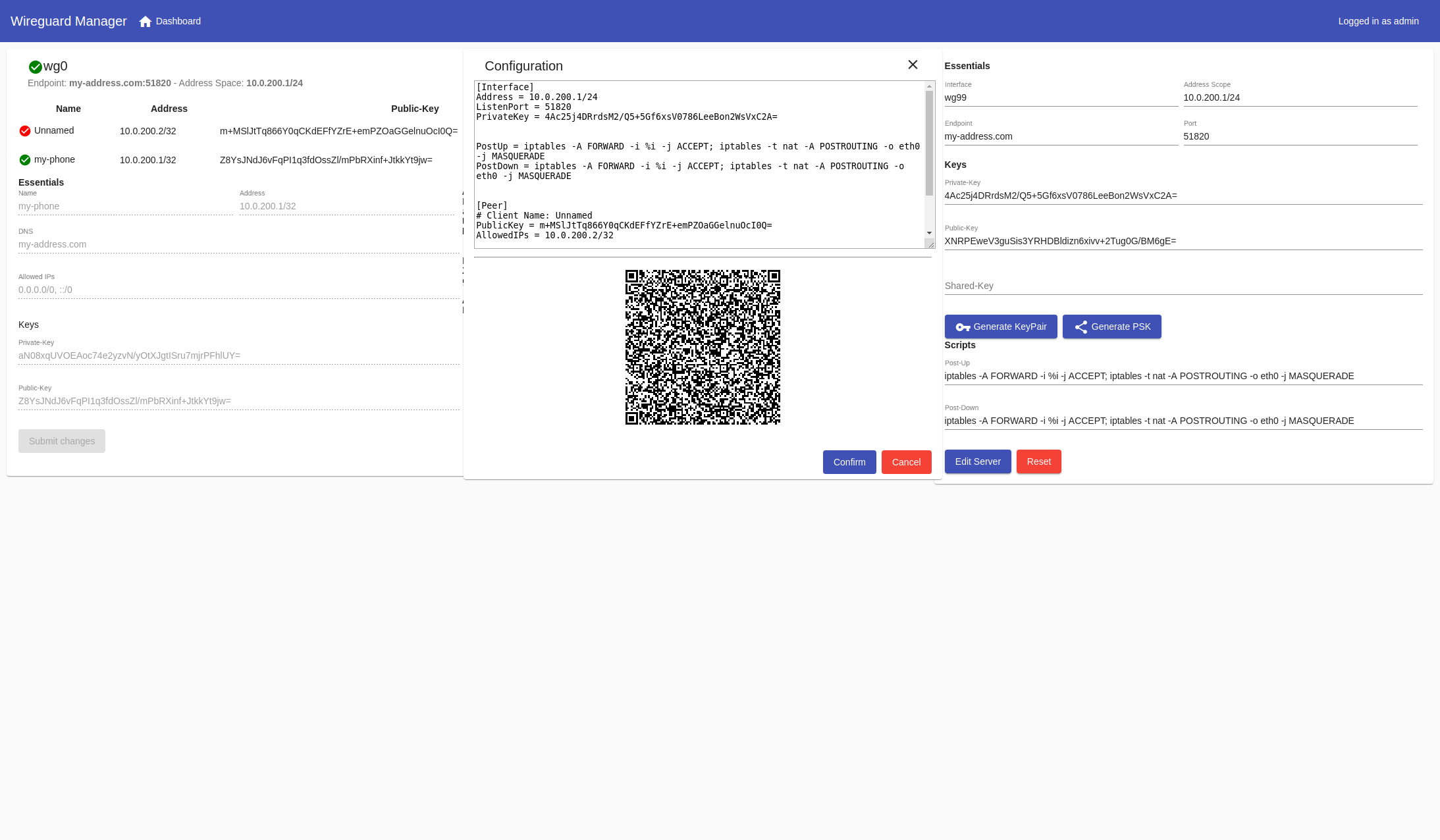
- Export server config, along with client config as zip.
Peer
- Create/Delete/Modify
- Bandwidth usage statistics
- Export by QRCode, Text
- Authentication via API-Keys for automation (Created in GUI)
General
- Modify Admin User
Dependencies
- Linux >= 5.6 (Alternatively: wireguard-dkms)
Common Installation Steps
- Enable ip forwarding:
sysctl -w net.ipv4.ip_forward=1 # IPV4 Support sysctl -w net.ipv6.conf.all.forwarding=1 # IPV6 Support - For persistent configuration:
cat > /etc/sysctl.d/99-sysctl.conf << EOF net.ipv4.ip_forward = 1 net.ipv6.conf.all.forwarding=1 EOF - It is recommended to have a firewall protecting your servers
Notes
- A few people has experienced issues with running the dockerized method using bridged networking. To fix this, you can use
network_mode: host. Note that you can no longer reverse-proxy the web interface from reverse proxies such as jwilder/nginx-proxy.
Method #1: Docker-compose
version: "2.1"
services:
wireguard:
container_name: wg-manager
image: perara/wg-manager
restart: always
sysctls:
net.ipv6.conf.all.disable_ipv6: 0 # Required for IPV6
cap_add:
- NET_ADMIN
#network_mode: host # Alternatively
ports:
- 51800-51900:51800-51900/udp
- 8888:8888
volumes:
- ./wg-manager:/config
environment:
HOST: 0.0.0.0
PORT: 8888
ADMIN_PASSWORD: admin
ADMIN_USERNAME: admin
WEB_CONCURRENCY: 1
Method #2: Bare Metal
Using the development branch
As there is no builds for the development branch, you have to do the following:
Change image: perara/wg-manager to
build:
context: https://github.com/perara/wg-manager.git#dev
Guides
Usage
When docker container/server has started, go to http://localhost:8888
API Docs
The API docs is found here.
API-Keys
- Login to wg-manager
- Go to edit profile
- Create API-Key and take note of the key. Use the X-API-Key header to authenticate.
- Example:
curl -i -H "X-API-Key: <key-goes-here>" http://<host>:<port>/api/v1/users/api-key/list - Example 2:
curl -X POST "http://<host>:<port>/api/v1/peer/add/configuration" -H "accept: application/json" -H "Content-Type: application/json" -H "X-API-Key: <api-key-here>" -d "{\"server_interface\":\"wg0\"}"
Environment variables
| Environment | Description | Recommended |
|---|---|---|
| GUNICORN_CONF | Location of custom gunicorn configuration | default |
| WORKERS_PER_CORE | How many concurrent workers should there be per available core (Gunicorn) | default |
| WEB_CONCURRENCY | The number of worker processes for handling requests. (Gunicorn) | 1 |
| HOST | 0.0.0.0 or unix:/tmp/gunicorn.sock if reverse proxy. Remember to mount | 0.0.0.0 |
| PORT | The port to use if running with IP host bind | 80 |
| LOG_LEVEL | Logging level of gunicorn/python | info |
| ADMIN_USERNAME | Default admin username on database creation | admin |
| ADMIN_PASSWORD | Default admin password on database creation | admin |
| POST_UP | The POST_UP Command (version 4) | default |
| POST_DOWN | The POST_DOWN Command (version 4) | default |
| POST_UP_V6 | The POST_UP Command (version 6) | default |
| POST_DOWN_V6 | The POST_DOWN Command (version 6) | default |
Showcase
Roadmap
Primaries
- Implement multi-server support (setting up site-2-site servers from the GUI)
- Extending multi-server support to enable custom access lists (A peer can be assigned to multiple servers, as part of the ACL)